Table of Contents
Updated by 10.02.2024
Securely Taking Credit Card Payments Over the Phone: A Step-by-Step Guide
As businesses strive to provide seamless and convenient payment options, accepting payments over the phone with technology like E-Complish’s Call Sentry and secured custom ePayment Link utilized via SMS, chat, and email has become common practice.
With touch-tone tech, Interactive Voice Response Payments (IVR payments), and secured payment links, customers enter their card or banking information and complete transactions 24/7 without assistance from customer service representatives.
As with most card-not-present transactions, there is always a risk of data breaches, identity theft, and fraud if you accept credit card payments or debit card payments over the phone.
So, let’s discuss the state of call center security and the steps needed to safeguard your customer’s data and business’s reputation when using IVR payments.
Why Should Certain Businesses Opt for Accepting Phone Payments?
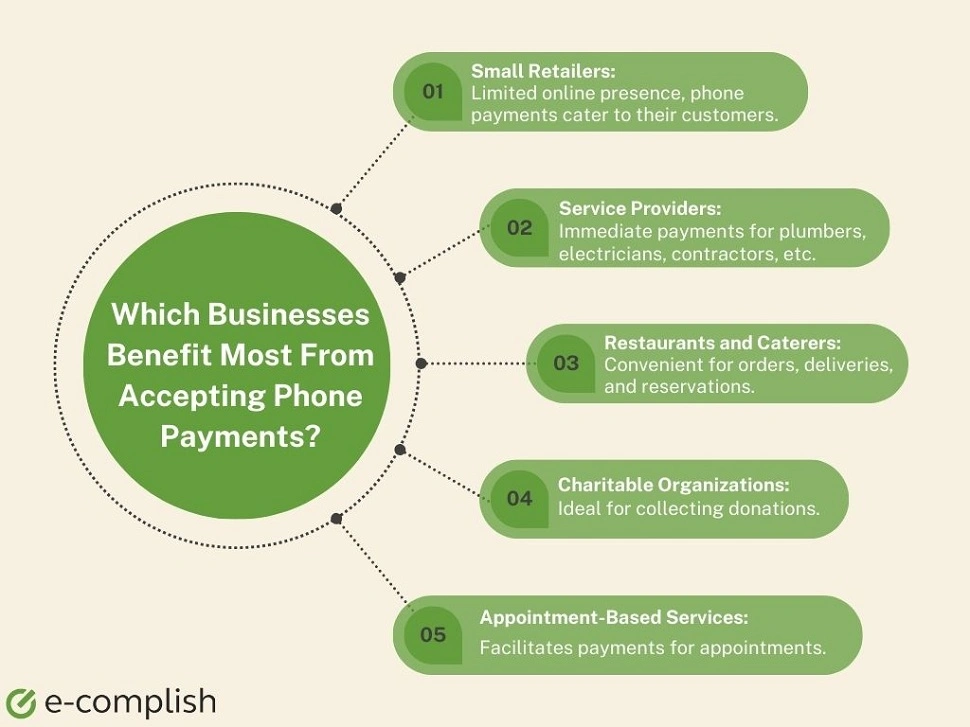
Businesses with high transaction volumes catering to customers constantly moving or having limited internet access benefit significantly from over-the-phone payments. IVR payments suit e-commerce, healthcare, financial services, utility, subscription-based, retail stores, food delivery services, transport services, and more.
As it is, 81% of consumers want more self-service options. And over-the-phone transactions are easy to use – even for non-tech-savvy customers, allowing them to pay when they want with minimal inconvenience.
In terms of ROI, consulting firm McKinsey says, “Next-generation IVR systems deliver a fivefold improvement in customer satisfaction scores, accelerate issue resolution, and reduce the number of live-agent calls by more than 5%.”
The Road to Customer Loyalty Runs Through Call Center Security
For every trusted resource, there is a bad actor trying to take advantage of it.
And that is the catch-22 of call centers: the pivotal role they play across various industries also makes them an attractive target for fraudsters seeking to exploit and capture sensitive customer information.
“The call center is a prime target,” Marc Hopkins, VP at E-Complish, tells PYMNTS. “[Call centers] come into contact with quite a bit of sensitive customer data, whether its credit card credentials or business banking and savings accounts … all of which can be exploited.”
Call center fraud generally takes two primary forms: an attack from the inside or a third party intercepting data from a point of weakness.
With insider threats, the threat originates from within the call center itself. Unscrupulous employees or representatives may compromise customer data, either for personal gain or to sell it on the black market for fraudulent purposes.
Data interception involves capturing data as it is being transmitted between the customer and the call center representative. Fraudsters often exploit weaknesses in the data transmission process to access sensitive information.
Protecting call centers against fraud requires a multi-pronged approach that incorporates technology and proactive measures to lock down any and all attack vectors.
Organizations need to remember that if they have built a 12-foot wall, fraudsters, and bad actors are working in the background on building a 13-foot ladder.
Understanding Call Center Fraud and Safeguarding Call Centers

“The first step is taking that sensitive data out of the hands of your call center,” Hopkins said.
One way to do so is by implementing an automated payment assistant, like E-Complish’s Call Sentry, during customer interactions. Automated assistants can significantly reduce the risk of data exposure by allowing customers to input their sensitive information without the call center representative hearing it.
This technology effectively removes the sensitive data from the hands of call center personnel, reducing the likelihood of insider threats, Hopkins said.
He added that another prominent way to safeguard call centers from fraudulent activity is by providing customers with secured payment links via SMS, email, or chat to ensure their data remains safe during transactions.
These links are typically time-sensitive and can be used to make payments while on the call with a representative. This method enhances data security and customer convenience.
Allowing customers to interact with automated payment systems through outbound calls can further protect sensitive data. This method ensures that customer information remains secure and minimizes the risk of insider threats within the call center.
“Outbound calls completely take the sensitive customer data out of the hands of the call center and protect it from any fraudulent activity,” said Hopkins.
Leveraging Advanced Verification Technologies
Protecting call centers and the sensitive data they handle against fraud is crucial in today’s business landscape, and as fraudsters become more sophisticated, organizations are turning to more advanced technologies themselves.
Traditional verification methods, such as passwords, PINs, and Social Security numbers, are increasingly vulnerable due to their availability on the black market, which is why businesses are interested in leveraging advanced verification technologies to protect and secure sensitive data.
While these technologies are still evolving, they promise more robust customer verification. Hopkins noted that they include future-fit technologies such as biometrics, voice recognition and eye/fingerprint scanning, and artificial intelligence (AI) powered identity verifications that use real-time behavioral analytics and behavior mapping.
Verifying that somebody is who they say they are leads to a smoother interaction and a shorter call to the call center, Hopkins explained, which ideally creates better customer experiences by removing potential frictions and has the downstream effect of driving greater loyalty.
After all, the ideal call center experience prioritizes Payment Card Industry Data Security Standard (PCI DSS) compliance to ensure the secure handling of sensitive payment information.
This protocol ensures sensitive data is safeguarded against fraudulent activities and — importantly — creates a customer-first experience through automated payment assistants, secured payment links, and advanced verification technologies that streamline customer interactions, reducing call times and enhancing overall customer convenience.
Step-by-Step Guide on How to Make Phone Payments Secure

In an ever-evolving digital landscape, staying ahead of call center fraud is not only necessary but also a strategic advantage that can build customer loyalty and business success.
With ever-present cyber threats, it’s crucial to have a step-by-step guide to guarantee the safety and efficiency of your customer contact center.
Our user-friendly guide offers simple and effective strategies to enhance payment security, giving you peace of mind and your customers a seamless experience.
Step 1: Account Setup
As a business owner, you want to provide customers with a smooth and secure ACH, debit card, or credit card payment experience. That’s where setting up a merchant account comes in if you don’t already have one. A merchant account is a type of account that allows businesses to process ACH and card payments.
It acts as a secure payment gateway, connecting your business to your customers’ banking accounts and card issuers for payment processing.
Step 2: Utilizing a Virtual Terminal
Virtual terminals act as a bridge between your customers and payment processors. The virtual terminal securely collects and encrypts your customer’s card payment information, then transmits it to the payment processor for authorization without needing physical payment terminals.
In the case of IVR phone payments, virtual terminals integrate with the IVR system to automate the payment process. With E-Complish’s virtual terminal, customers call the DirectPay IVR system and enter their payment credentials using their telephone keypad, and the virtual terminal securely transmits the customer’s card information to the payment processor for authorization, ultimately speeding up the payment process.
Step 3: Collecting Payment Details
Securely taking card payments over the phone is a straightforward process.
There are two secure options for obtaining the customer’s payment credentials. The first is E-Complish’s CallSentry, where the automated payment attendant securely captures customer credentials for the processing of their payment. The other option is a securely generated payment link via E-Complish’s virtual terminal, that can be texted (SMS) or emailed to the customer for secure payment processing.
Step 4: Processing the Payment
The consequences of inadequate data security measures can be severe, leading to financial loss, identity theft, and damaging reputation. Therefore, businesses must adopt robust security protocols such as encryption, secure storage, multi-factor authentication, and regular security audits.
Moreover, compliance with industry standards and data security and privacy regulations, such as PCI DSS (Payment Card Industry Data Security Standard) and NACHA, is crucial. Adhering to these standards protects customers’ data and helps your business build trust and credibility with clients.
Step 5: Issuing a Payment Receipt
Issuing a digital payment receipt via email, SMS, or other means is vital for businesses and customers as it provides transparency and verification for financial transactions. It is a crucial document that serves as proof of payment received by your business, protecting against disputes or errors.
Additionally, it helps with reconciliation purposes, bank-required proof of authorization, and chargeback management assistance. Overall, it ensures trust and transparency between the parties involved.

Step 6: Maintaining Accurate Records
Accurate records help with accounting, dispute resolution, and compliance. Having a clear record of all phone payments makes tracking payments easier, preventing disputes and ensuring compliance with regulations.
Equally important is implementing security measures to protect stored records from unauthorized access, data breaches, or loss, including using secure systems, limiting access to confidential information, and regularly backing up data.
Step 7: Ensuring Data Security
Inadequate security protocols increase the vulnerability of confidential payment data and may result in theft or misuse. Therefore, it is necessary to implement robust and trustworthy measures to protect the privacy and integrity of such information.
This entails utilizing encryption techniques for secure data transmission, implementing tokenization methods, securing networks and devices, and consistently updating security protocols. By taking these precautions, you can make paying with card over the phone and via ACH safer, reducing the potential for financial theft and fraud.
Unlock Seamless Phone Payment Solutions with E-Complish!
By following the best practices outlined, businesses can seamlessly implement secure phone payments and build trust and confidence with their customers. Now that you know how to take payments over the phone in a safe manner, you might be looking for a secure phone payment provider.
E-Complish can help you unlock a world of seamless, secure, and reliable payment solutions, including over-the-phone payments. Streamline your customer service experience with our user-friendly automated phone payment systems! Contact us to find out more.
FAQs
Is it safe to take card payments over the phone?
What payment methods can I accept over the phone?
What should I do if a payment over the phone is declined?
Table of Contents

